Tor (used to stand for "
The Onion Router", but it's no longer considered an abbreviation, so it's just "
Tor"), is an anonymity network, used to surf the web (and more) anonymously. Basically, anyone running the Tor software on their computer runs a proxy, and traffic gets passed (encrypted) from one person running Tor to another person running Tor, multiple times through many users, until it get's to the page that you requested. Hence the term "
Onion" used to describe it, since it works in "
layers". Each person running Tor on their computer is called a "
Node".
To the page (and anyone logging requests to that page, such as the website owner for example) they can only see the IP address of the last Node (called the "end node"). Any communication along the way, between you, when you request the website page, and the final destination, is encrypted, and cannot be analyzed. However, the last Node in the chain can log and view traffic through it, if the person running it is unscrupulous, so for that reason it can't be said that Tor is 100% anonymous.
TOR Auto-install Shellscript
#!/bin/sh
echo "deb http://deb.torproject.org/torproject.org wheezy main" >> /etc/apt/sources.list
clear scr
echo "[*] Installing the keys...."
gpg --keyserver keys.gnupg.net --recv 886DDD89
gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
echo "Ready!!"
clear scr
echo "[*] Updating Repositories...."
apt-get update
clear scr
echo "[*] Installing TOR"
apt-get install deb.torproject.org-keyring
apt-get install tor
echo "Ready!!"
echo "[*] Installing Vidalia"
apt-get install vidalia
echo "Ready!!"
echo "[*] Installing iceweasel-torbutton"
apt-get install iceweasel-torbutton
echo "Ready!!"
clear scr
echo "[*] Installing Privoxy"
apt-get install privoxy
echo "[*] Configuring privoxy"
echo "forward-socks5 / 127.0.0.1:9050 ." >> /etc/privoxy/config
echo "Ready!!"
service tor restart
service privoxy restart
echo "Tor has been installed successfully."
Save this script to a file like torinstall.sh and chmod +x it.
#chmod +x torinstall.sh
#./torinstall.sh











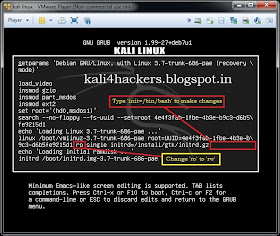
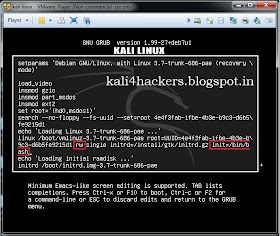
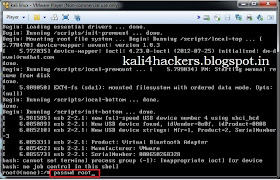











 and then on Computer.
and then on Computer.