As kali linux is new to all of us, being a learner we all come with a new issue and try to resolve it as quickly as possible. While installing software, most of us don't know the dependency packages that are installed or removed from the system. A great feature that kali linux provide is that when we run apt command, it checks the available package/s in the repository and accordingly asks if to install. Meanwhile, it also checks the un-necessary packages that is not required. Here is a command that removes the un-necessary packages. From the root terminal window, please type apt-get autoremove. When you hit 'return' or 'enter' key, it checks the packages that is to be removed from the system. Please read those packages carefully, before you make confirmation to remove it from the system.
Friday, 31 May 2013
Wednesday, 29 May 2013
Installing Firefox on Kali Linux
Mozilla Firefox is a quite handy browser compared to Iceweasel (default browser in Kali Linux). It has lot of plug-in features that Iceweasel lag. Sometimes, we find it difficulty while navigating through Iceweasel. Hence, I thought of installing Mozilla Firefox. To do this, you have to first un-install Iceweasel from Kali Linux or else it won't allow you to install Mozilla Firefox. Here are the step that I performed.
1. Open root terminal window and type
apt-get remove iceweasel
it removes iceweasel from the application menu
2. type echo -e "\ndeb http://downloads.sourceforge.net/project/ubuntuzilla/mozilla/apt all main" | tee -a /etc/apt/sources.list > /dev/null
it adds repository for the installation
3. type apt-key adv --recv-keys --keyserver keyserver.ubuntu.com C1289A29
import the required gpg key
4. type apt-get update
update the required package
5. type apt-get install firefox-mozilla-build
install mozilla firefox on your sytem
6. type firefox on terminal window to start working with mozilla firefox
1. Open root terminal window and type
apt-get remove iceweasel
it removes iceweasel from the application menu
2. type echo -e "\ndeb http://downloads.sourceforge.net/project/ubuntuzilla/mozilla/apt all main" | tee -a /etc/apt/sources.list > /dev/null
it adds repository for the installation
3. type apt-key adv --recv-keys --keyserver keyserver.ubuntu.com C1289A29
import the required gpg key
4. type apt-get update
update the required package
5. type apt-get install firefox-mozilla-build
install mozilla firefox on your sytem
6. type firefox on terminal window to start working with mozilla firefox
Monday, 27 May 2013
How to install qbittorrent in Kali Linux
About qbittorrent: qbittorrent is a torrent client, an alternative to utorrent. It's a GUI based cross platform free software based on Qt toolkit.
We know that Kali Linux's base package is constructed in Debian, so we need to add http://http.packages.debian.org to sources.list file. To do this,
1. open any text editor and edit sources.list file, located in /etc/apt directory, with an entry deb http://http.packages.debian.org import deb packages.
3. Once qbittorrent is installed, type qbittorrent on the root terminal window and press enter
We know that Kali Linux's base package is constructed in Debian, so we need to add http://http.packages.debian.org to sources.list file. To do this,
1. open any text editor and edit sources.list file, located in /etc/apt directory, with an entry deb http://http.packages.debian.org import deb packages.
2. type apt-get install qbittorrent on the root terminal window and press enter
and, you are set to go.
BackTrack vs. Kali Linux
As we know Kali Linux is the successor of BackTrack 5, so there are much similarities to BackTrack in many ways, but it lays a new foundation and makes substantial improvements that will allow it to be even more useful to penetration testers in the coming years.
BackTrack
Many security practitioners have been using BackTrack to perform their security assessments. BackTrack is an open-source Linux-based penetration testing toolset. BackTrack made performing a security assessment easier because all of the common tools that you needed were all packaged into one nice distribution and ready to go at a moment's notice. BackTrack contains so many security tools that it is too difficult to list them all. If you want to see a complete list of all the tools just run "dpkg --list". BackTrack made it easy to create a new VM from the downloaded ISO, perform the assessment, then either archive that VM for future reference or delete it when done to remove the evidence. The latest version of BackTrack is version 5 release 3 and it came out on August 13, 2012. If you want to explore this version, you can download it from this site. But before, you do, check out Kali Linux first.
Kali Linux
Kali Linux is a new open source distribution that facilitates penetration testing. Whereas BackTrack was built on Ubuntu, Kali Linux is built from scratch and constructed on Debian and is FHS-compliant. Kali Linux also has improved software repositories that are synchronized with the Debian repositories so it makes it easier to keep it updated, apply patches and add new tools. It is also easy to customize your own Kali Linux so that it contains only the packages and features that are required. You can also customize your desktop environment to use Gnome(default), KDE, LXDE, XFCE or whatever you prefer.
The development of Kali Linux was funded by Offensive Security. Offensive Security is a security training and penetration testing consulting firm that has been a creator, supporter and maintainer of BackTrack since the beginning. For years they have offered their popular Penetration Testing with BackTrack (PWB) class, but with the introduction of Kali Linux, that class name will likely change.
To get your hands on the latest Kali Linux distribution, you can download it from: http://www.kali.org/downloads or http://cdimage.kali.org.
Kali Linux offers documentation at http://docs.kali.org, bug reporting at http://bugs.kali.org and a Kali forum site at http://forums.kali.org.
Labels:
backtrack,
dpkg,
FHS,
GNOME,
kali linux,
KDE,
offensive security,
PWB,
release
Add Repository in Kali Linux
Kali linux is a debian base linux distribution designed for penetration testing. Here, I will give a tutorial on how to add a repository on Kali Linux 1.0.3 with ease. Repository is a archival software, where software in this archive can be retrieved by the user to use. Please click here to check for the new blog post on repository.
1. Open root terminal and type this code.
root@kali:~# leafpad /etc/apt/sources.list
2. Add all repositories, i.e. :
deb http://http.kali.org/ /kali main contrib non-free
deb http://http.kali.org/ /wheezy main contrib non-free
deb http://http.kali.org/kali kali-dev main contrib non-free
deb http://http.kali.org/kali kali-dev main/debian-installer
deb http://http.kali.org/kali kali main contrib non-free
deb http://http.kali.org/kali kali main/debian-installer
deb-src http://http.kali.org/kali kali-dev main contrib non-free
deb-src http://http.kali.org/kali kali main contrib non-free
deb-src http://security.kali.org/kali-security kali/updates main contrib non-free
Save the file and exit.
Save the file and exit.
3. root@kali:~# apt-get update
4. root@kali:~# apt-get upgrade
Saturday, 25 May 2013
Armitage in Kali Linux
About Armitage
Armitage is a scriptable red team collaboration tool for Metasploit that visualizes targets, recommends exploits and exposes the advanced post-exploitation features in the framework. Through one Metasploit instance, your team will:
- Use the same sessions
- Share hosts, captured data, and downloaded files
- Communicate through a shared event log
- Run bots to automate red team tasks
Armitage is open source software developed by Raphael Mudge's company Strategic Cyber LLC. However, Cobalt Strike is the commercially supported big brother of Armitage.
Armitage organizes Metasploit's capabilities around the hacking process. There are features for discovery, access, post-exploitation, and maneuver. This section describes these features at a high-level, the rest of this manual covers these capabilities in detail.
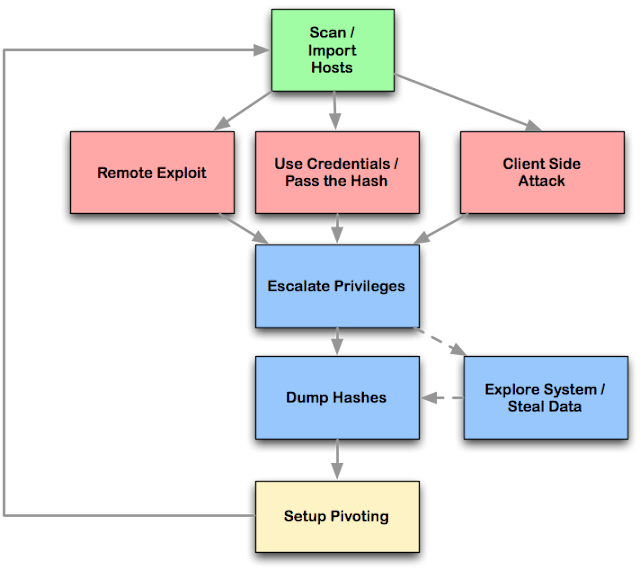 Armitage's dynamic workspaces let you define and switch between target criteria quickly. Use this to segment thousands of hosts into target sets. Armitage also launches scans and imports data from many security scanners. Armitage visualizes your current targets so you'll know the hosts you're working with and where you have sessions.
Armitage's dynamic workspaces let you define and switch between target criteria quickly. Use this to segment thousands of hosts into target sets. Armitage also launches scans and imports data from many security scanners. Armitage visualizes your current targets so you'll know the hosts you're working with and where you have sessions.
Armitage recommends exploits and will optionally run active checks to tell you which exploits will work. If these options fail, use the Hail Mary attack to unleash Armitage's smart automatic exploitation against your targets.
Once you're in, Armitage exposes post-exploitation tools built into the Meterpreter agent. With the click of a menu you will escalate your privileges, log keystrokes, dump password hashes, browse the file system, and use command shells.
Armitage makes it trivial to setup and use pivots. You'll use compromised hosts as a hop to attack your target's network from the inside. Armitage uses Metasploit's SOCKS proxy module to let you use external tools through your pivots. These features allow you to maneuver through the network.
The rest of this manual is organized around this process, providing what you need to know in the order you'll need it.
Package dependency before you install Armitage
Armitage exists as a client and a server that allow red team collaboration to happen. The Armitage client package is made available for Windows, MacOS X, and Linux. Armitage does NOT require a local copy of the Metasploit Framework to connect to a team server.
These getting started instructions are written assuming that you would like to connect to a local instance of the Metasploit Framework.
Armitage requires the following:
- Metasploit Framework and its dependencies.
- PostgreSQL Database
- Nmap
- Oracle's Java 1.7
To quickly install all of the dependencies, you have a few options:
- Use a Linux distribution for penetration testing such as Kali Linux.
- These distributions ship with Metasploit and its dependencies installed for you.
- Use the MSF Installer Script created by DarkOperator (This option will setup an environment that uses Git for updates).
- Use the official installer provided by Rapid7 (This option will require you to register with Rapid7 to get updates).
Setup Instructions to install Armitage in Kali Linux
- Open a terminal
- Initialize the database: service metasploit start
- Stop the metasploit service: service metasploit stop
- Extract armitage: tar zxvf armitageDDMMYY.tgz, where DDMMYY is version or date when armitage has launched.
How to Start Armitage
- Open root terminal
- type apt-get install armitage
Before you start Armitage, make sure the postgresql database is running:
- type service postgresql start
If you get a missing database.yml error, type:
- type service metasploit start
Thursday, 23 May 2013
A brief tutorial on GRUB boot loader
A boot loader is a software program that runs when a computer boot. It's responsible for loading and transferring control to an operating system kernel software. The kernel, in turn, initializes the rest of the operating system.
GRUB (GRand Unified Boot-loader) or GNU GRUB is a very powerful multi-boot loader, which can load a wide variety of free operating systems, as well as proprietary operating systems with chain-loading. GRUB is designed to address the complexity of booting a personal computer. One of the important features in GRUB is flexibility; GRUB understands filesystems and kernel executable formats, so you can load an arbitrary operating system the way you like, without recording the physical position of your kernel on the disk. Thus you can load the kernel just by specifying its file name and the drive and partition where the kernel resides.

When booting with GRUB, you can use either a command-line interface or a menu interface. Using the command-line interface, you type the drive specification and file name of the kernel manually. In the menu interface, you just select an OS using the arrow keys. The menu is based on a configuration file which you prepare beforehand. While in the menu, you can switch to the command-line mode and vice-versa. You can even edit menu entries before using them.
Contents of GRUB
Installed programs:
grub-bios-setup, grub-editenv, grub-fstest, grub-install, grub-kbdcomp, grub-menulst2cfg, grub-mkconfig, grub-mkimage, grub-mklayout, grub-mknetdir, grub-mkpasswd-pbkdf2, grub-mkrelpath, grub-mkrescue, grub-mkstandalone, grub-ofpathname, grub-probe, grub-reboot, grub-script-check, grub-set-default, grub-sparc64-setup
Installed programs:
grub-bios-setup, grub-editenv, grub-fstest, grub-install, grub-kbdcomp, grub-menulst2cfg, grub-mkconfig, grub-mkimage, grub-mklayout, grub-mknetdir, grub-mkpasswd-pbkdf2, grub-mkrelpath, grub-mkrescue, grub-mkstandalone, grub-ofpathname, grub-probe, grub-reboot, grub-script-check, grub-set-default, grub-sparc64-setup
Installed directories:
/usr/lib/grub, /etc/grub.d, /usr/share/grub, /boot/grub
Short Descriptions
grub-bios-setup Is a helper program for grub-install
grub-editenv A tool to edit the environment block
grub-fstest Tool to debug the filesystem driver
grub-install Install GRUB on your drive
grub-kbdcomp Script that converts an xkb layout into one recognized by GRUB
grub-menulst2cfg Converts a GRUB Legacy menu.lst into a grub.cfg for use with GRUB 2
grub-mkconfig Generate a grub config file
grub-mkimage Make a bootable image of GRUB
grub-mklayout Generates a GRUB keyboard layout file
grub-mknetdir Prepares a GRUB netboot directory
grub-mkpasswd-pbkdf2 Generates an encrypted PBKDF2 password for use in the boot menu
grub-mkrelpath Makes a system pathname relative to its root
grub-mkrescue Make a bootable image of GRUB suitable for a floppy disk or CDROM/DVD
grub-mkstandalone Generates a standalone image
grub-ofpathname Is a helper program that prints the path of a GRUB device
grub-probe Probe device information for a given path or device
grub-reboot Sets the default boot entry for GRUB for the next boot only
grub-script-check Checks GRUB configuration script for syntax errors
grub-set-default Sets the default boot entry for GRUB
grub-sparc64-setup Is a helper program for grub-setup
EDIT GRUB File
GRUB configuration file is located in grub directory. Pathname: /boot/grub/grub.cfg. This file is required when you want to change the order in boot menu.
Kali Linux's Penetration Testing Tools
Kali Linux is an advanced Penetration Testing and Security Auditing Linux distribution. It is the most advanced and versatile penetration testing distribution ever created. Kali Linux comes with bundles of penetration testing tools. In GUI, you can find these tools in drop-down menu list, i.e. Applications --> Kali Linux. The Top 10 Security Tools are in top list. Other tools are categorized according to their functionality.

Saturday, 18 May 2013
What is SET?
SET stands for Social Engineering Toolkit, primarily written by David Kennedy(ReL1K). The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET was designed to be released with the http://www.social-engineer.org launch and has quickly became a standard tool in a penetration testers arsenal. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
To start SET, either you goto Applications --> Kali Linux --> Exploitation Tools --> Social Engineering Toolkit --> se-toolkit. (This command was valid till Kali Linux ver. 1.0.4, now it changed to setoolkit in Kali Linux ver 1.0.5 and 1.0.6).
- it will set new config environment
- check for SET software update
- verifying the software
- start SET Menu

SET is a menu driven based attack system, which is fairly unique when it comes to hacker tools. The decision not to make it command line was made because of how social-engineer attacks occur; it requires multiple scenarios, options, and customizations. If the tool had been command line based it would have really limited the effectiveness of the attacks and the inability to fully customize it based on your target.
Friday, 17 May 2013
FHS (File-system Hierarchy Standard) in Kali Linux
Filesystem Hierarchy Standard (FHS) defines the directory structure and directory contents in Linux operating systems. Based on Debian-package compliance, Kali Linux follows FHS. This means it allows all Linux users to easily locate binaries, support files, libraries, etc. Kali Linux has more than 300 penetration testing tools and you will be able to call any tool from anywhere on the system as every application is included in the system path. Unlike Backtrack, you do not have to navigate, just type the command name of the tool in root terminal and you are set to go.
Wednesday, 1 May 2013
WPScan in Kali Linux
WPScan is a WordPress vulnerability scanner written in ruby, which is capable of detecting common security vulnerabilities as well as listing all plugins used by a website hosting WordPress. WPScan is pre-installed in Kali Linux.
WPscan is a nice tool if you want to find out how to exploit a WordPress site as it does all of this:
- Username enumeration (Checks the ‘author’ query-string and the location header).
- Weak password cracking (This can be multi-threaded and supplied a password list of your choosing).
- Version enumeration (Finds what version of WordPress they are running by checking meta tags and client side files).
- Vulneralbility enumeration (Based on what version they are running).
- Timbthumb file enumeration (Checks for Timthumb exploit).
- Plugin enumeration (See what plugins they are running).
- Plugin vulneralbility enumeration (Tells you which, if any, plugins are vulnerable to exploits).
- Theme enumeration (What theme are they running. Sometimes you can find exploits in the theme).
- Readme.html enumeration (Sometimes can be useful because you will see what is needed for that theme. Helps you find out what they are running. E.G. “This theme require PHP 5″).
- Directory listing (Helps footprint the WordPress installation).
To start WPScan, click on Applications--> Kali Linux--> Web Applications--> Web Vulnerability Scanners--> wpscan
Now, to scan for wordpress plugin to exploit, let pickup any wordpress plugin, ex.: http://www.cretan-snails.com. Type
root@kali:~# ruby /usr/bin/wpscan --url http://www.cretan-snails.com in the root terminal window;
(A)

(B)

From the above screenshots, we found that there is 1 vulnerability and 13 plug-ins from passive detection. To find Wordpress usernames, type root@kali:~# wpscan --url http://www.cretan-snails.com --enumerate user
(C)


The above screenshot reveals that there 10 Wordpress usernames from http://www.cretan-snails.com
(A)

(B)

From the above screenshots, we found that there is 1 vulnerability and 13 plug-ins from passive detection. To find Wordpress usernames, type root@kali:~# wpscan --url http://www.cretan-snails.com --enumerate user
(C)


The above screenshot reveals that there 10 Wordpress usernames from http://www.cretan-snails.com
Labels:
cracking,
enumeration,
exploit,
kali linux,
plugin,
ruby,
WordPress,
WPScan
Location:
Kolkata, West Bengal, India










